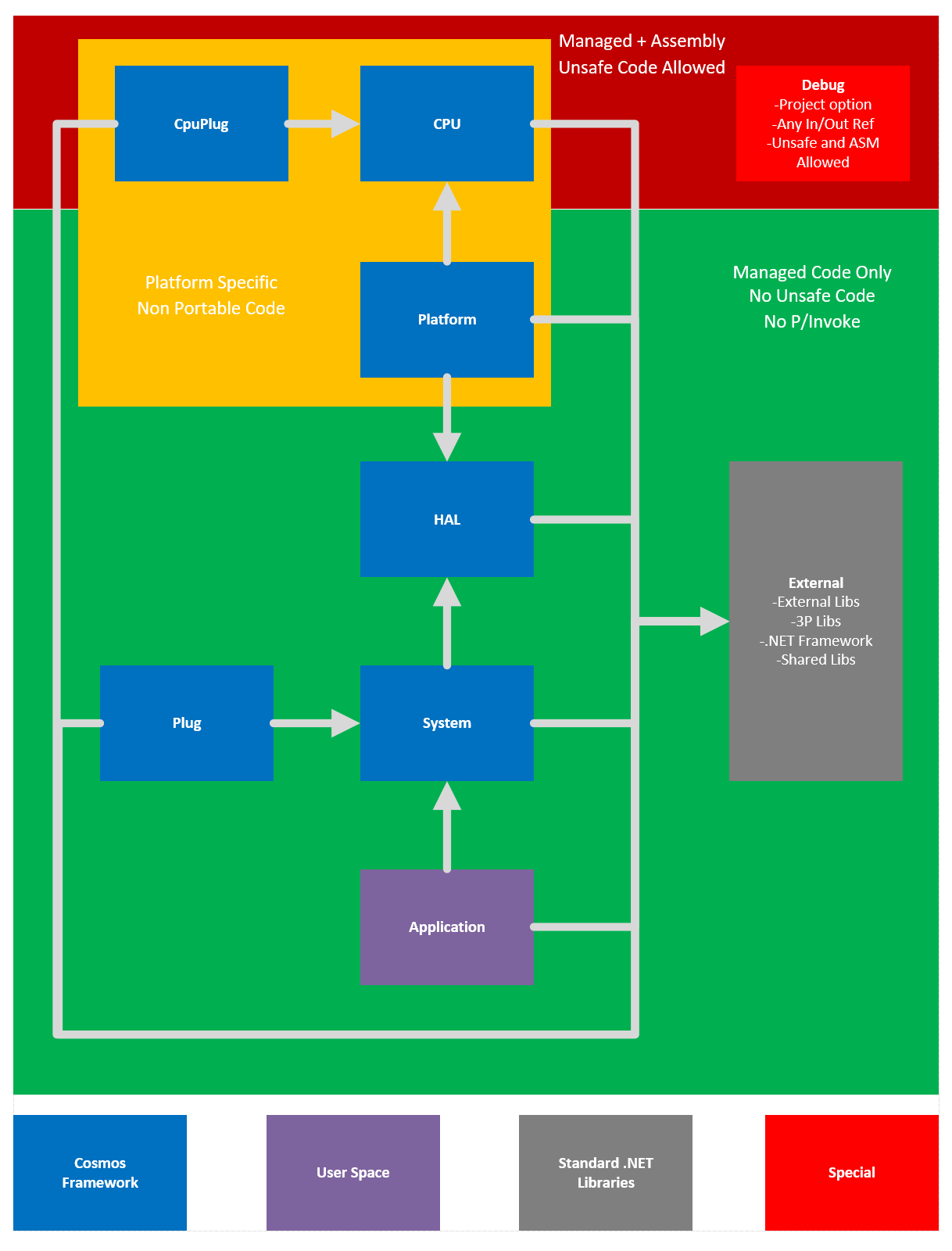
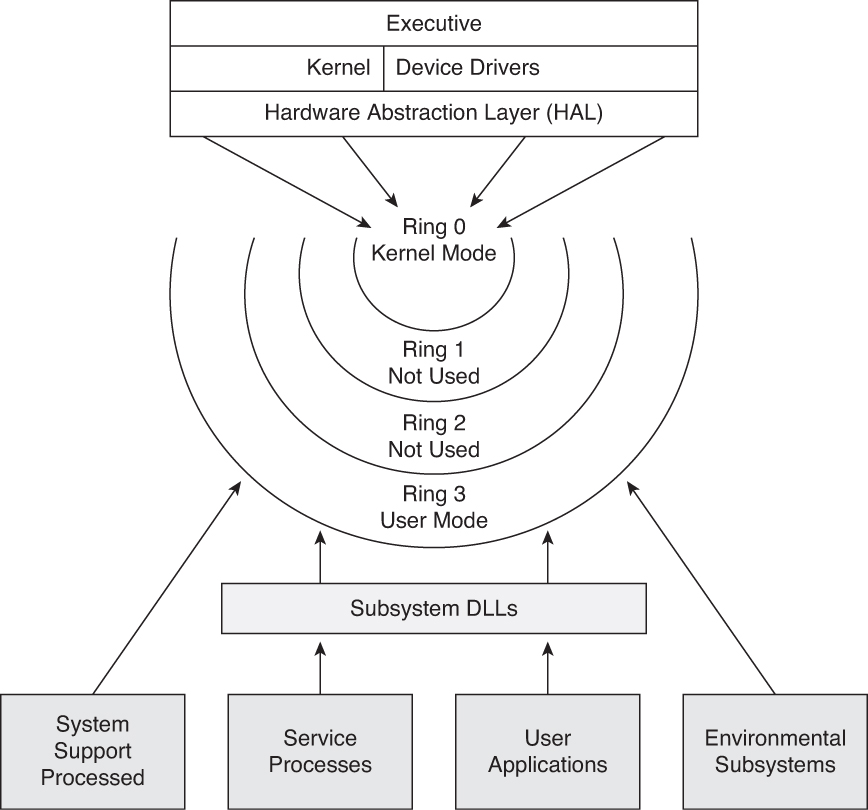
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium

🎯 Kernel Of Ring Homomorphism || Definition Of Ker (f) Definition of Kernel Of Ring Homomorphis 🎯 - YouTube
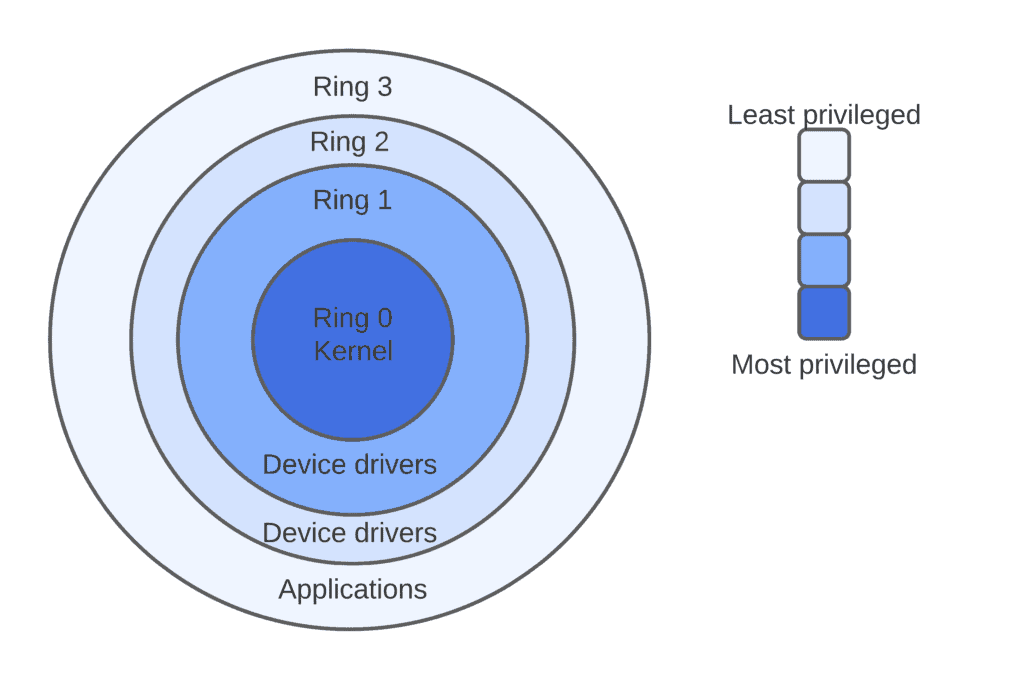
Operating system privilege rings in most modern hardware platforms and... | Download Scientific Diagram
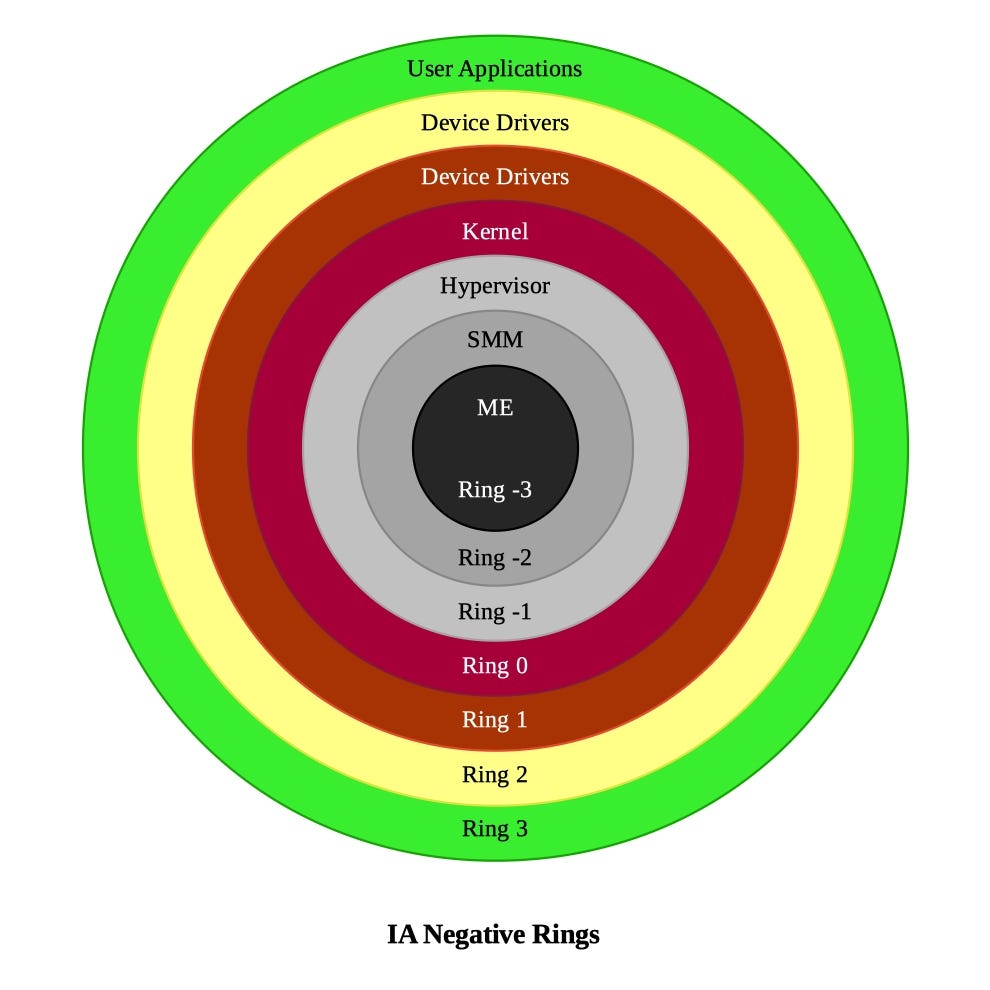
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium
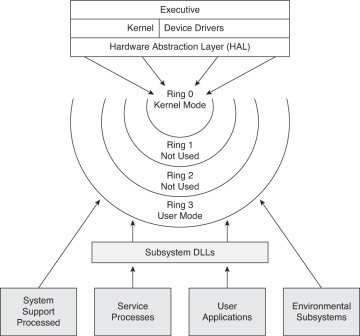
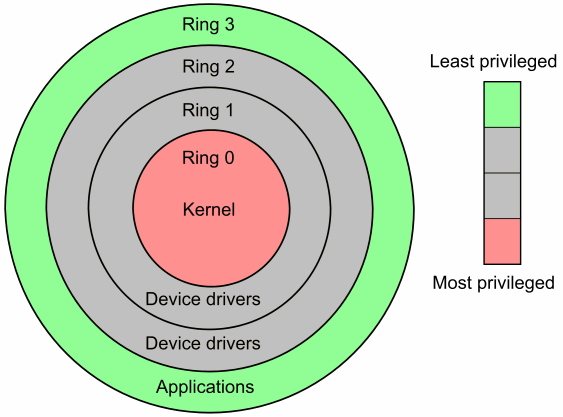
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification

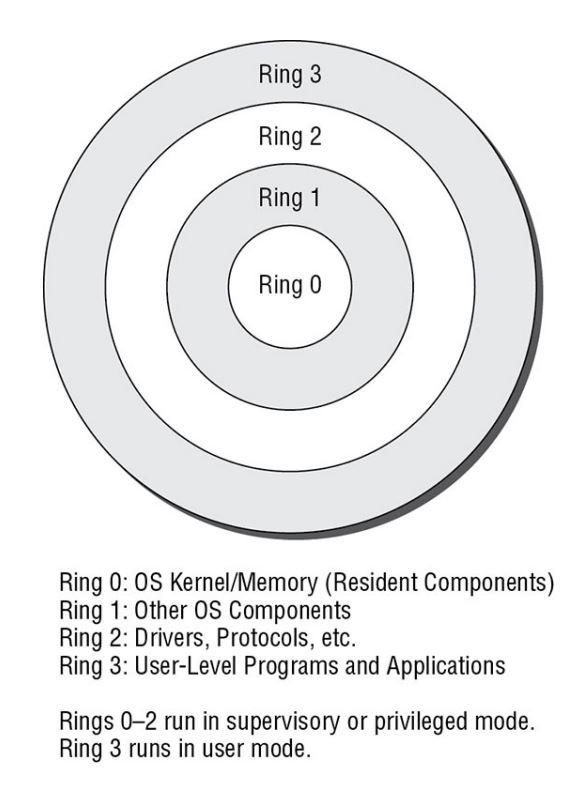
4). CHAP 9 - PROTECTION MECHANISMS: I.Protection Rings: 0123/II. Operational States: Queues, Scheduler, Ready, Waiting, Running, Supervisory, Stopped/III. Sec Modes: Dedicated-System high-Compartmented-Multilevel /IV. Operating Modes: User, Privileged ...





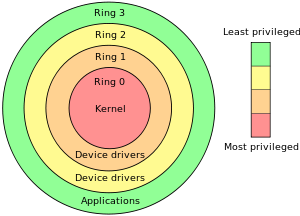
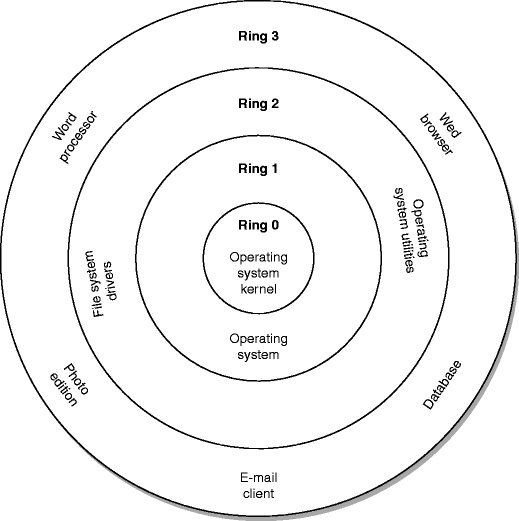


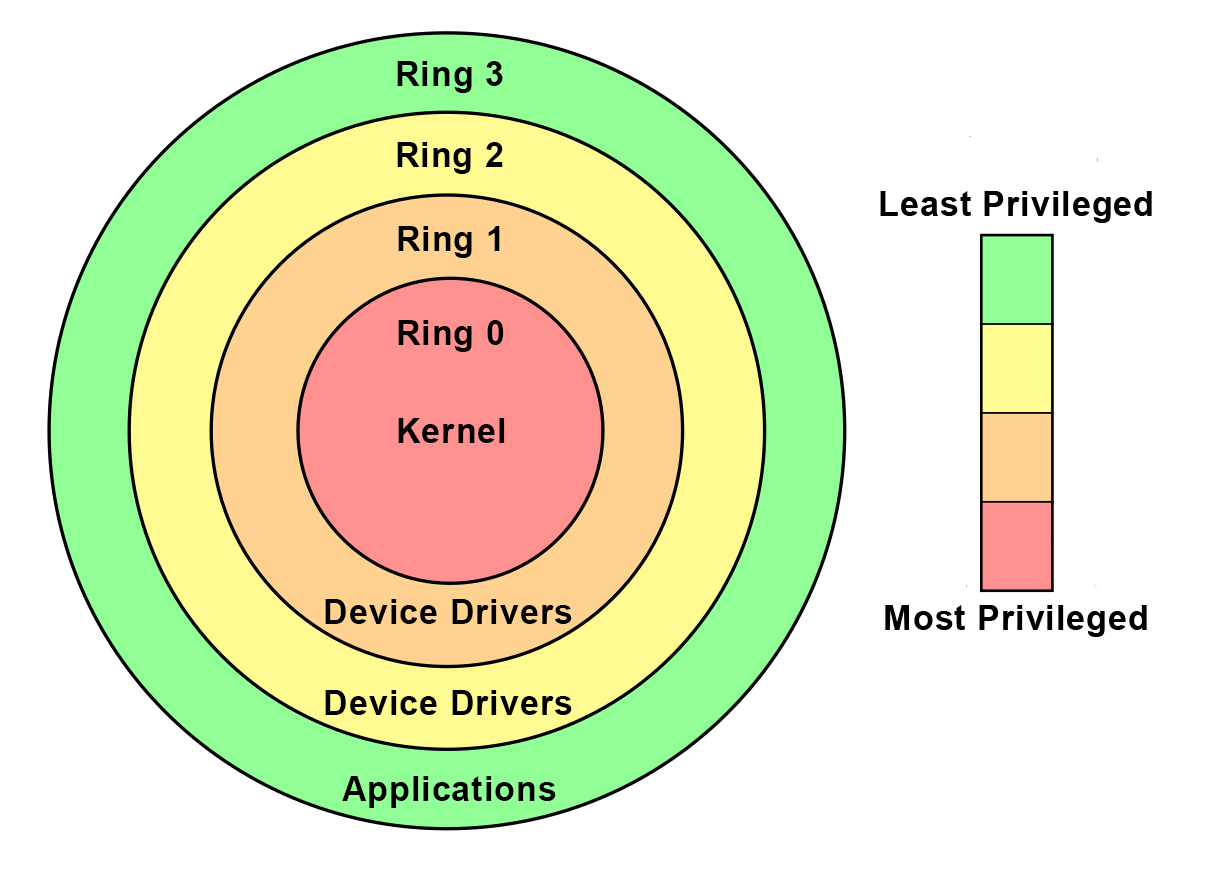
![Intel's Ring Architecture [28, 37, 24, 14] | Download Scientific Diagram Intel's Ring Architecture [28, 37, 24, 14] | Download Scientific Diagram](https://www.researchgate.net/publication/50875025/figure/fig2/AS:671525288038404@1537115513180/Intels-Ring-Architecture-28-37-24-14.png)